Published On Streamed live on Mar 14, 2024
/// 🔗 Register for future webcasts, summits, and workshops here - https://blackhillsinfosec.zoom.us/ze/...
🛝 🔗 Webcast Slides –
https://www.blackhillsinfosec.com/wp-...
From multiplate layers of obfuscation to conditional behavior to sandbox avoidance, malware can indeed be complicated.
But ultimately, when a Windows malware event occurs, the most important questions are “if” and “how” it impacted your environment!
In this free one-hour Black Hills Information Security (BHIS) webcast, Patterson Cake - Incident Responder, will discuss a simplified approach and tactical tips for answering those questions when investigating malware events on your Windows endpoints.
Chat with your fellow attendees in the Black Hills Infosec Discord server here: / discord -- in the #🔴webcast-live-chat channel.
///Chapters
0:00 Introduction
3:55 Agenda and schedule
5:12 Win-Mal Investigations
7:32 Malware analysis
11:20 Malware commonalities
12:40 Most common threats (recent)
18:13 Technical possibilities
20:24 Windows malware investigation - artifacts
22:19 Network communications (C2)*
25:01 Disk (“Writable”)*
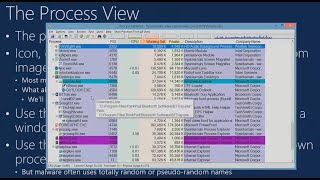
26:59 Running process (memory)
27:35 Services
28:25 Scheduled tasks
29:05 Running processes [DIFF]
32:34 Windows malware investigation collection
36:04 Win-Mal Investigation - WORKFLOW
46:30 Sandbox Analysis [FINDINGS]
48:08 Win-Mal Investigations [FINDINGS]
49:33 WinMal Technical Possibilities…
53:32 Q&A