Published On Jun 30, 2021
Learn tricks and techniques like these, with us, in our amazing training courses!
https://flashback.sh/training
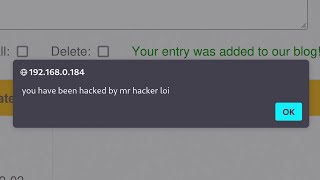
In this short video we show you how dangerous a cross site scripting (XSS) vulnerability can be.
Back in 2018, Pedro found 3 vulnerabilities that allow an unauthenticated attacker to achieve remote code execution as root in a Cisco Identity Services Engine device.
1- Stored cross site scripting (exploitable by an unauthenticated attacker)
2- Unsafe Java deserialization (exploitable by an authenticated user)
3- Privilege escalation to root due to incorrect file permissions
We start by sending an unauthenticated HTTP request to store the XSS payload on the device. Then, we send a phishing email to the device administrator. Once the device administrator clicks on the email link, he will be sent to the device page that contains our XSS payload. That payload sends a malicious request to a REST endpoint in the device that performs the Java deserialization, and we then get our shell running as the web server user. Finally we abuse the incorrect file permissions to get root!
For an in depth look on each vulnerability and how the exploit works under the hood, please check the advisory at https://github.com/pedrib/PoC/blob/ma...
CVE-2018-15440: Stored Cross-site Scripting
CVE-2017-5641: Unsafe Flex AMF Java Object Deserialization
SSD-3778: Privilege Escalation via Incorrect sudo and File Permission
Did you enjoy this video? Then follow us on Twitter, and subscribe to our channel for more awesome hacking videos.
~ Flashback Team
https://flashback.sh
/ flashbackpwn